Easy Collaboration
Real-time communication during audits is vital for both clients and pentesters. We hold that as a value.
Loading
Security Audits.
We think like attackers to help you stay ahead. Our Penetration Tests goes beyond checklists, they uncover real security risks that matter so you can fix them before they become a problem.
Real-time communication during audits is vital for both clients and pentesters. We hold that as a value.
Security threats constantly evolve. We keep up to date by actively doing cybersecurity research.
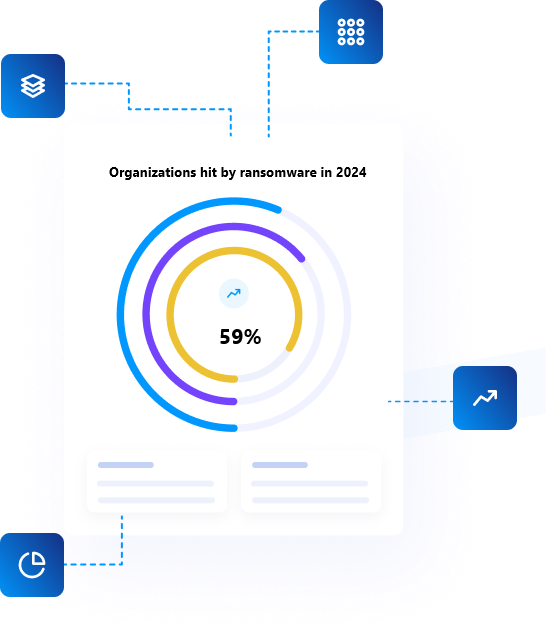
Our pentesters had reported vulnerabilities and audited several Fortune 500 companies. Take a look at our Hall of Fame
We believe that actively looking for vulnerabilities and sharing knowledge is the best way to keep us updated on the new threats.
With backgrounds in high-stakes security research, we've reported vulnerabilities in major tech companies, financial institutions, and government entities.